One of the (very minor) downsides of working from home, is that I often need to add my IP address to many network security groups (NSG) in Azure.
At the office, this isn't an issue because they have the benefit of a static IP address. At home however, my public IP can change on a regular basis.
I need to add my IP to the list of Inbound security rules, for port 3389 (RDP, so that I can use remote connection to access the machine):
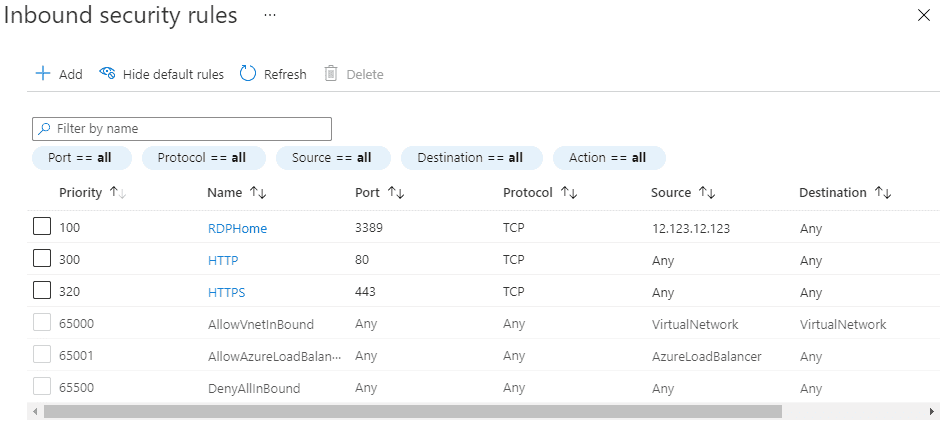
If this is a simple task, that I need to do every day, then why not automate it?
Setting things up
First thing we need to do is establish which NSG's we want to apply this to:
$nsgNames = @('My-nsg', 'Another-nsg')
$ruleName = "RDPHome"
$ruleDesc = "Allow RDP from my Home PC"
$rulePort = 3389We should be able to select the NSG by name, and then add the rule with the subsequent fields for each one.
We also need our public IP address. I wrote an article on how we can get that in powershell here: Getting your public IP address using Powershell. Short version, we can get it by calling this:
$myIP = (Invoke-WebRequest -uri "https://api.ipify.org/").ContentConnecting to Azure
Next, we need to connect to the Azure account:
Connect-AzAccountThis will bring up a separate window to log in, and then use those credentials for the rest of the script.
Creating/updating the rule
Let's now look at the method that will create/update the rule:
function AddOrUpdateRDPRecord {
Process {
$nsg = Get-AzNetworkSecurityGroup -Name $_
$ruleExists = (Get-AzNetworkSecurityRuleConfig -NetworkSecurityGroup $nsg).Name.Contains($ruleName);
if($ruleExists)
{
# Update the existing rule with the new IP address
Set-AzNetworkSecurityRuleConfig `
-Name $ruleName `
-Description $ruleDesc `
-Access Allow `
-Protocol TCP `
-Direction Inbound `
-Priority 100 `
-SourceAddressPrefix $myIp `
-SourcePortRange * `
-DestinationAddressPrefix * `
-DestinationPortRange $rulePort `
-NetworkSecurityGroup $nsg
}
else
{
# Create a new rule
$nsg | Add-AzNetworkSecurityRuleConfig `
-Name $ruleName `
-Description $ruleDesc `
-Access Allow `
-Protocol TCP `
-Direction Inbound `
-Priority 100 `
-SourceAddressPrefix $myIp `
-SourcePortRange * `
-DestinationAddressPrefix * `
-DestinationPortRange $rulePort
}
# Save changes to the NSG
$nsg | Set-AzNetworkSecurityGroup
}
}First, we check if a rule already exists with that name. If it does, we update it, otherwise we create a new rule.
Finally, we save changes to the NSG.
Now we just need to iterate over each NSG and apply the rule. Fortunately, we can do this with a single line:
$nsgNames | AddOrUpdateRDPRecordPutting it all together
Here is the full script, in order:
$nsgNames = @('My-nsg', 'Another-nsg')
$ruleName = "RDPHome"
$ruleDesc = "Allow RDP from my Home PC"
$rulePort = 3389
$myIp = (Invoke-WebRequest -uri "http://ifconfig.me/ip").Content
function AddOrUpdateRDPRecord {
Process {
$nsg = Get-AzNetworkSecurityGroup -Name $_
$ruleExists = (Get-AzNetworkSecurityRuleConfig -NetworkSecurityGroup $nsg).Name.Contains($ruleName);
if($ruleExists)
{
# Update the existing rule with the new IP address
Set-AzNetworkSecurityRuleConfig `
-Name $ruleName `
-Description $ruleDesc `
-Access Allow `
-Protocol TCP `
-Direction Inbound `
-Priority 100 `
-SourceAddressPrefix $myIp `
-SourcePortRange * `
-DestinationAddressPrefix * `
-DestinationPortRange $rulePort `
-NetworkSecurityGroup $nsg
}
else
{
# Create a new rule
$nsg | Add-AzNetworkSecurityRuleConfig `
-Name $ruleName `
-Description $ruleDesc `
-Access Allow `
-Protocol TCP `
-Direction Inbound `
-Priority 100 `
-SourceAddressPrefix $myIp `
-SourcePortRange * `
-DestinationAddressPrefix * `
-DestinationPortRange $rulePort
}
# Save changes to the NSG
$nsg | Set-AzNetworkSecurityGroup
}
}
Connect-AzAccount
$nsgNames | AddOrUpdateRDPRecord